Storm-2372 exploits device code multi-factor authentication flow.
Microsoft’s Threat Intelligence Center has discovered an ongoing device code phishing campaign by threat actor group identified as Storm-2372. This campaign has been active since August 2024, using messaging apps such as WhatsApp, Signal and Microsoft Teams to target government, non-governmental organizations (NGOs), information technology (IT) services and technology, defense, telecommunications, health, higher education, and energy/oil and gas in Europe, North America, Africa, and the Middle East.
How does device code authentication flow work?
In this attack “device code phishing, threat actors are capturing authentication tokens by exploiting the device code authentication flow of the target accounts. The device code authentication flow involves using a numeric or alphanumeric code to verify an account from a device with limited capabilities and since such devices cannot perform interactive authentication through a web flow, the authentication must be carried out on another device. In device code phishing attacks, malicious actors exploit this authentication flow.
During these attacks, the threat actor creates a legitimate device code request and tricks the target into entering it on a genuine sign-in page. This allows the actor to capture the authentication tokens (both access and refresh tokens) generated, which they then use to access the target’s accounts and data. Additionally, the phished authentication tokens can grant access to other services where the user has permissions, such as email or cloud storage, without needing a password. The threat actor maintains access as long as the tokens remain valid and can use the valid access token to move laterally within the environment.
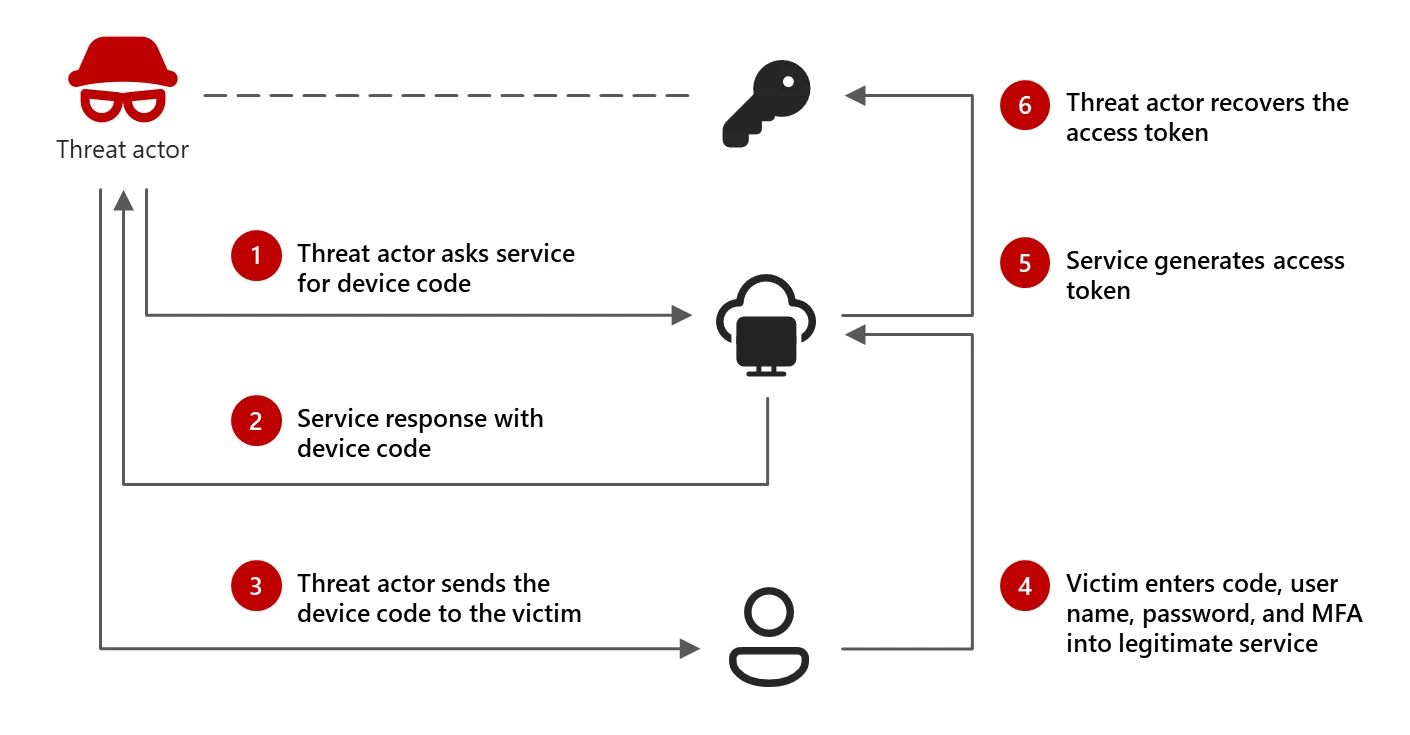
Early observations indicate that Storm-2372 likely targeted potential victims using third-party messaging services such as WhatsApp, Signal, and Microsoft Teams. The actors falsely posed as prominent figures relevant to the target to develop rapport before sending subsequent invitations to online events or meetings via phishing emails. These invitations lure the user into completing a device code authentication request, mimicking the experience of the messaging service. This provides Storm-2372 with initial access to victim accounts and enables them to perform Graph API data collection activities, such as email harvesting.

